Products
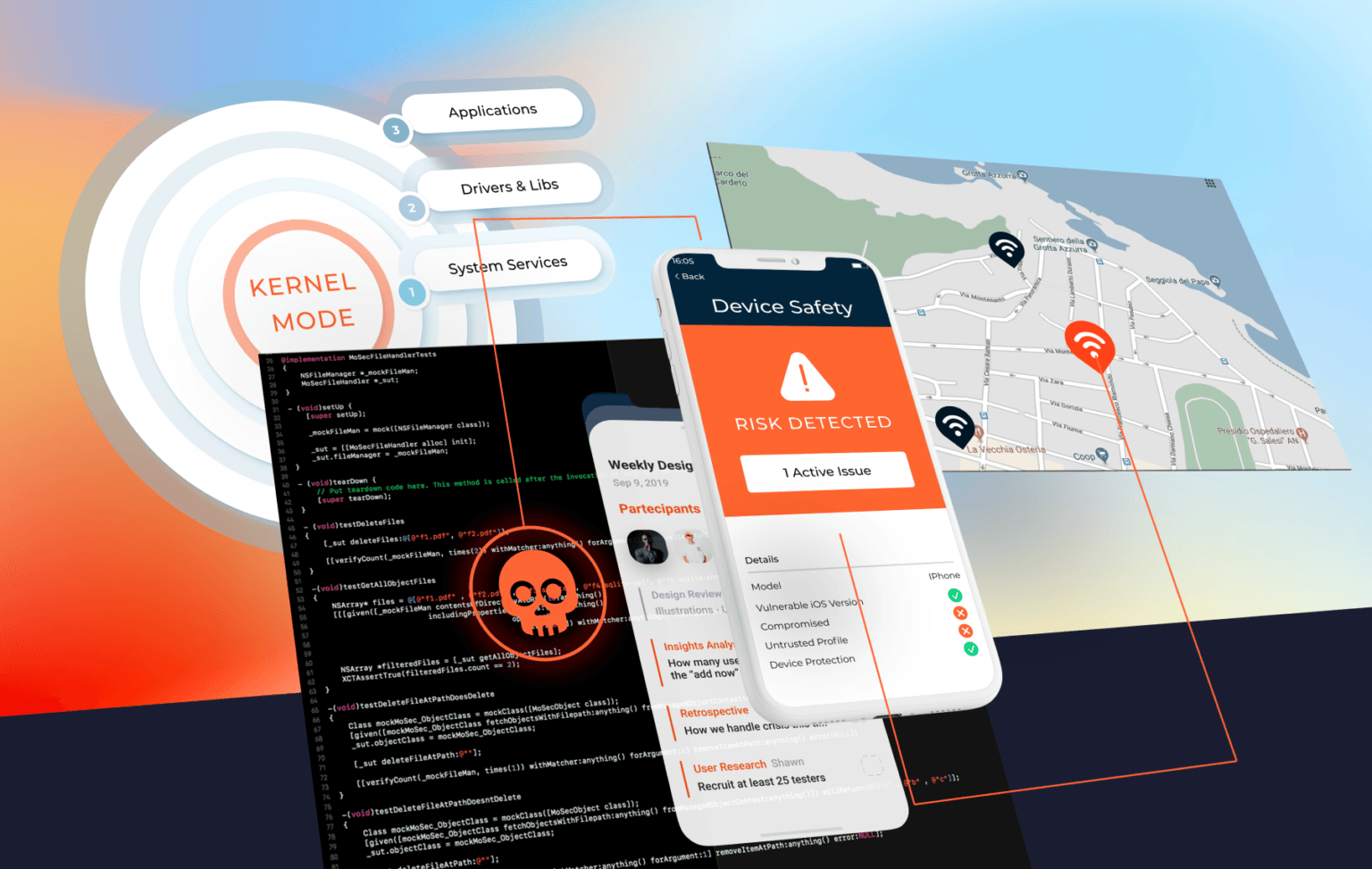
The selection is made by asking ourselves what would we choose to bet on if we had the same requirements. We carefully choose the products that we resell, taking into account every aspect that you might want covered when you invest in 3rd. Party technologies. We take into account the ripples effect across the risk surfaces of any solution that we either develop in-house or resell.
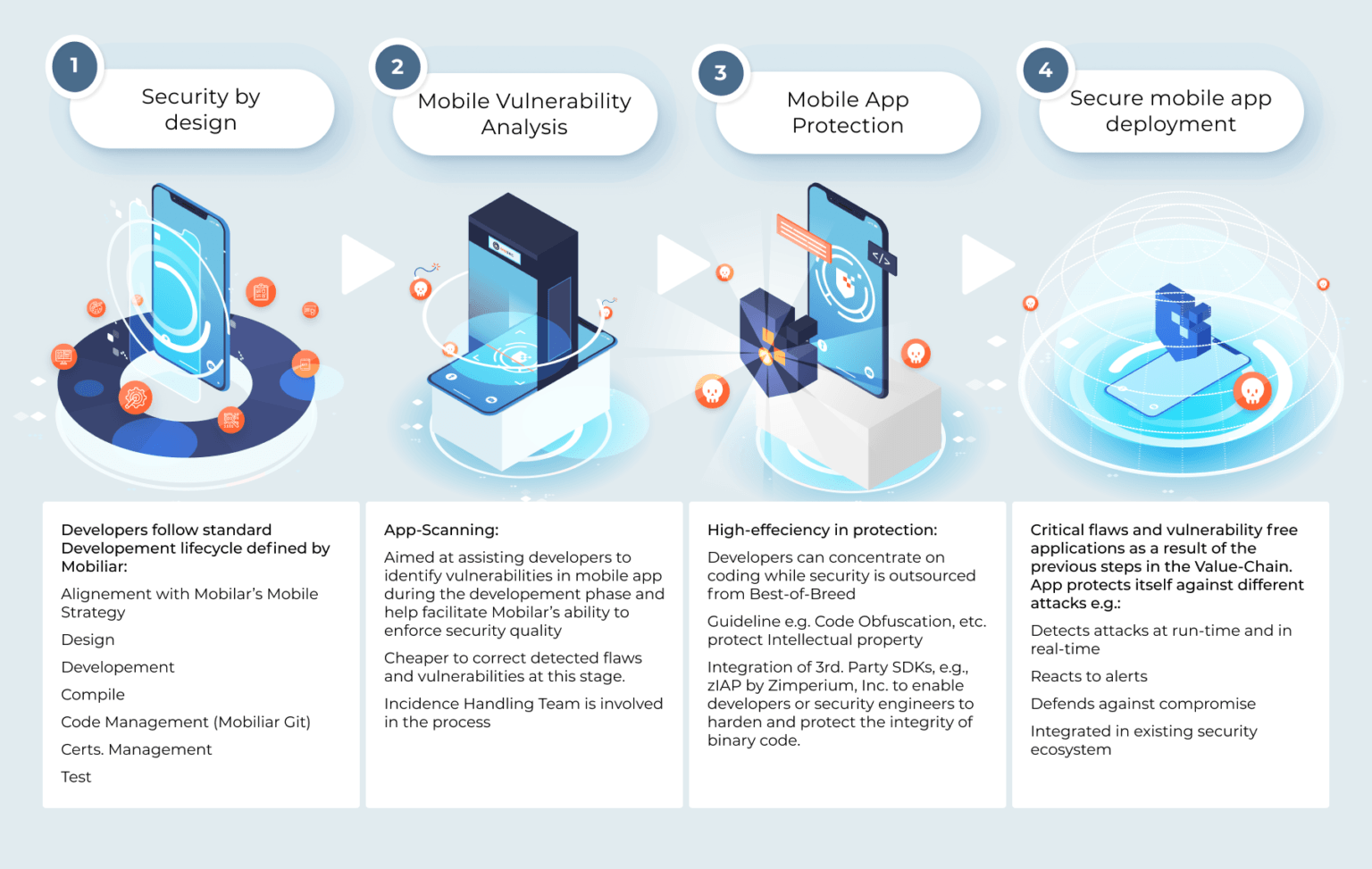
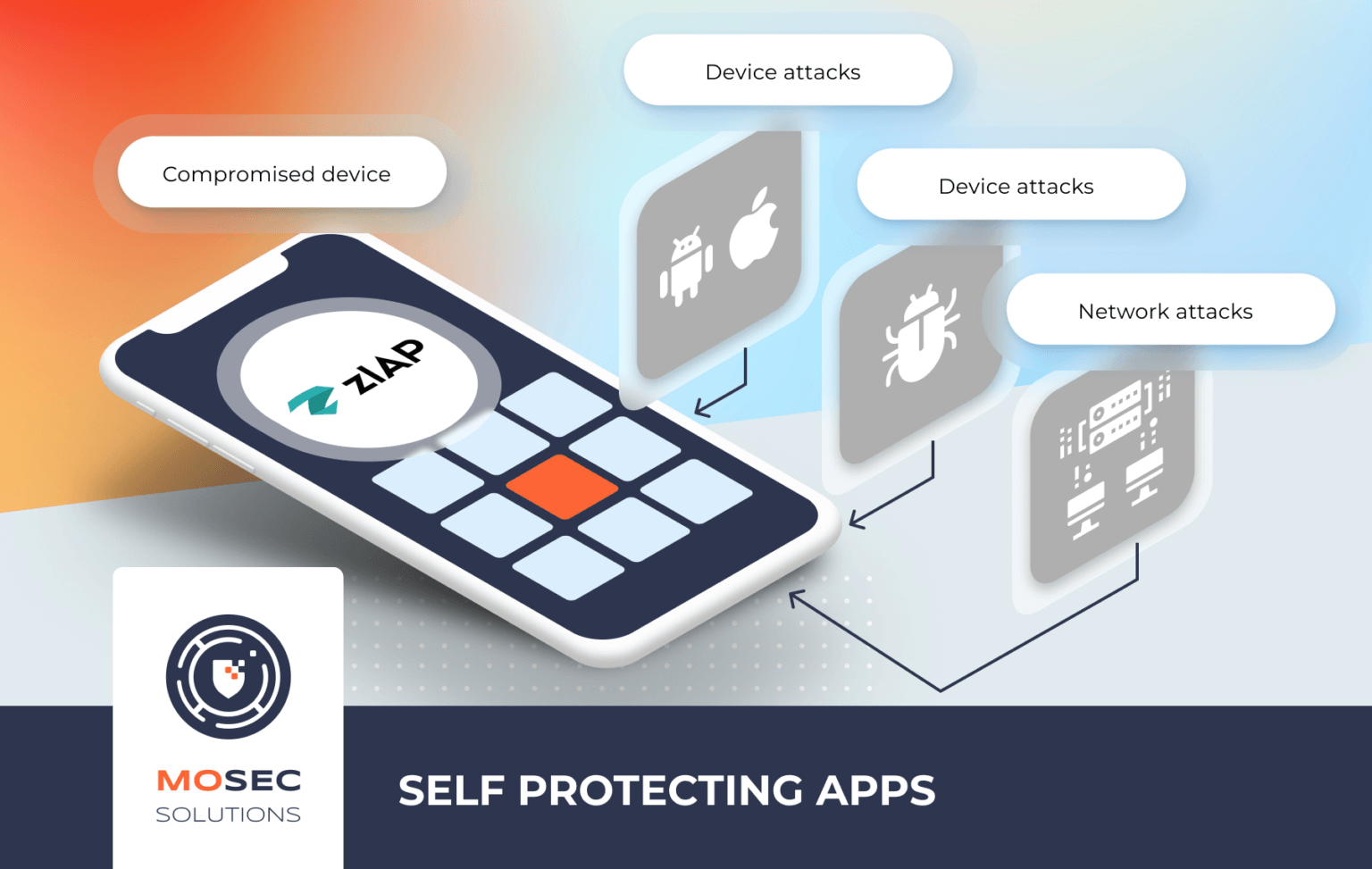
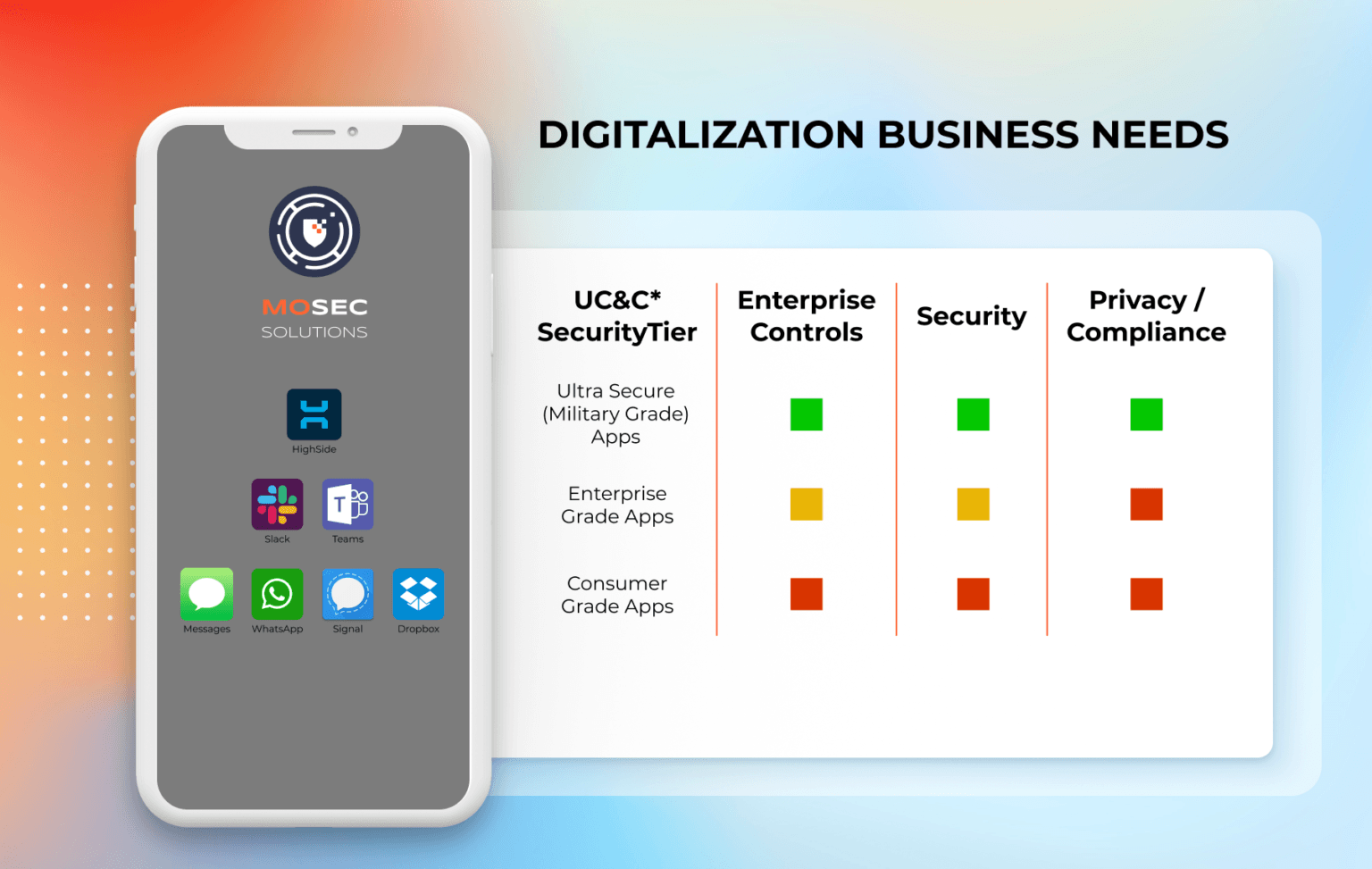
It is for this reason that we do not offer a bulk of solutions, but instead chose the best-in-class and planned to keep the list short strategically. Whether your company wishes to harden your mobile apps, by taking them through OWASP Top 10 for mobile apps or going a step further and integrating mobile security frameworks like Zimperium’s zIAP, MoSec Solutions strives to be a reliable partner. And if you were to consider a more reliable, simple, quick and secure mode of collaboration, we would have you up and running in no time with Hotshot as a corporate-grade secure zero trust collaboration tool.
contact us