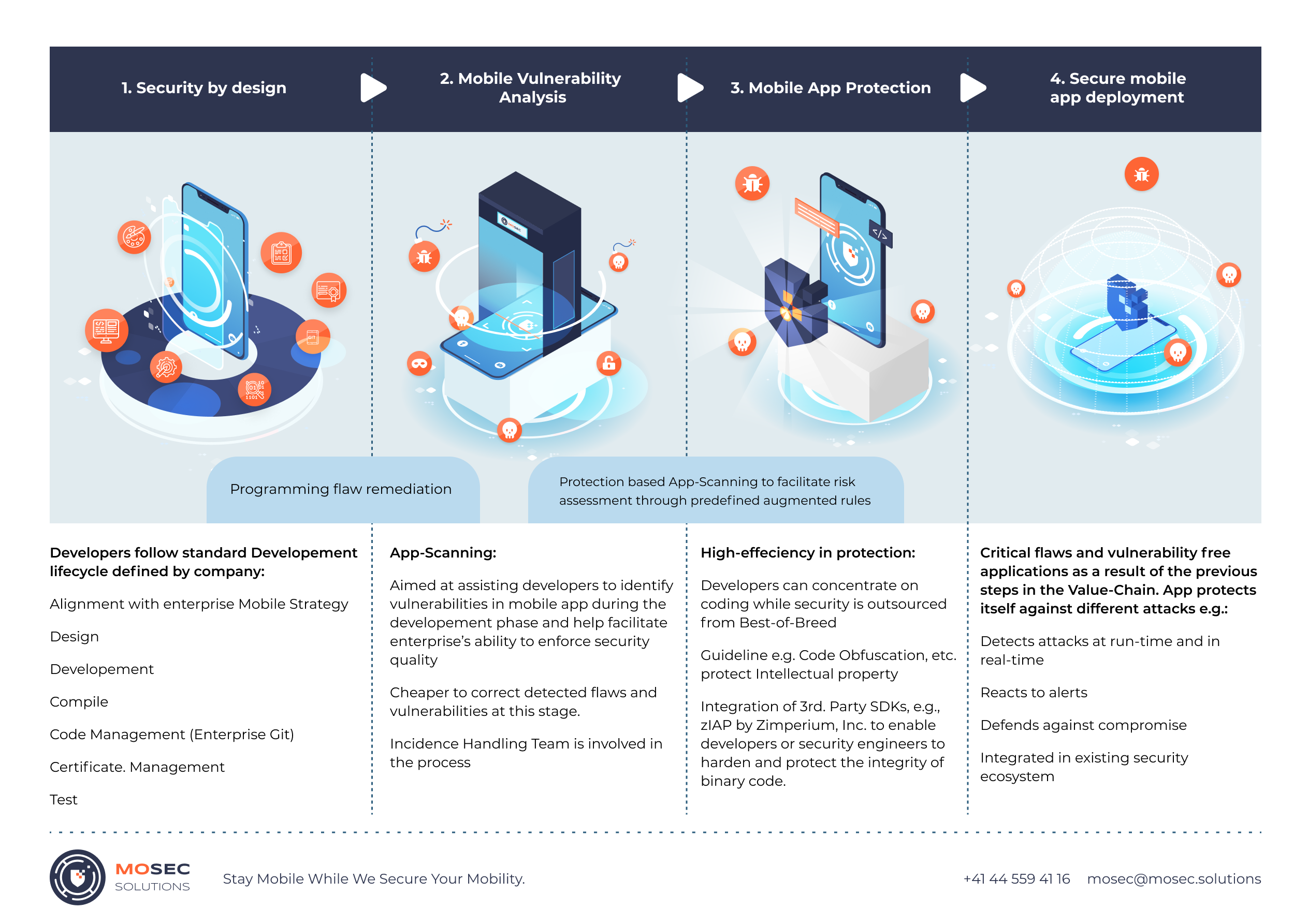
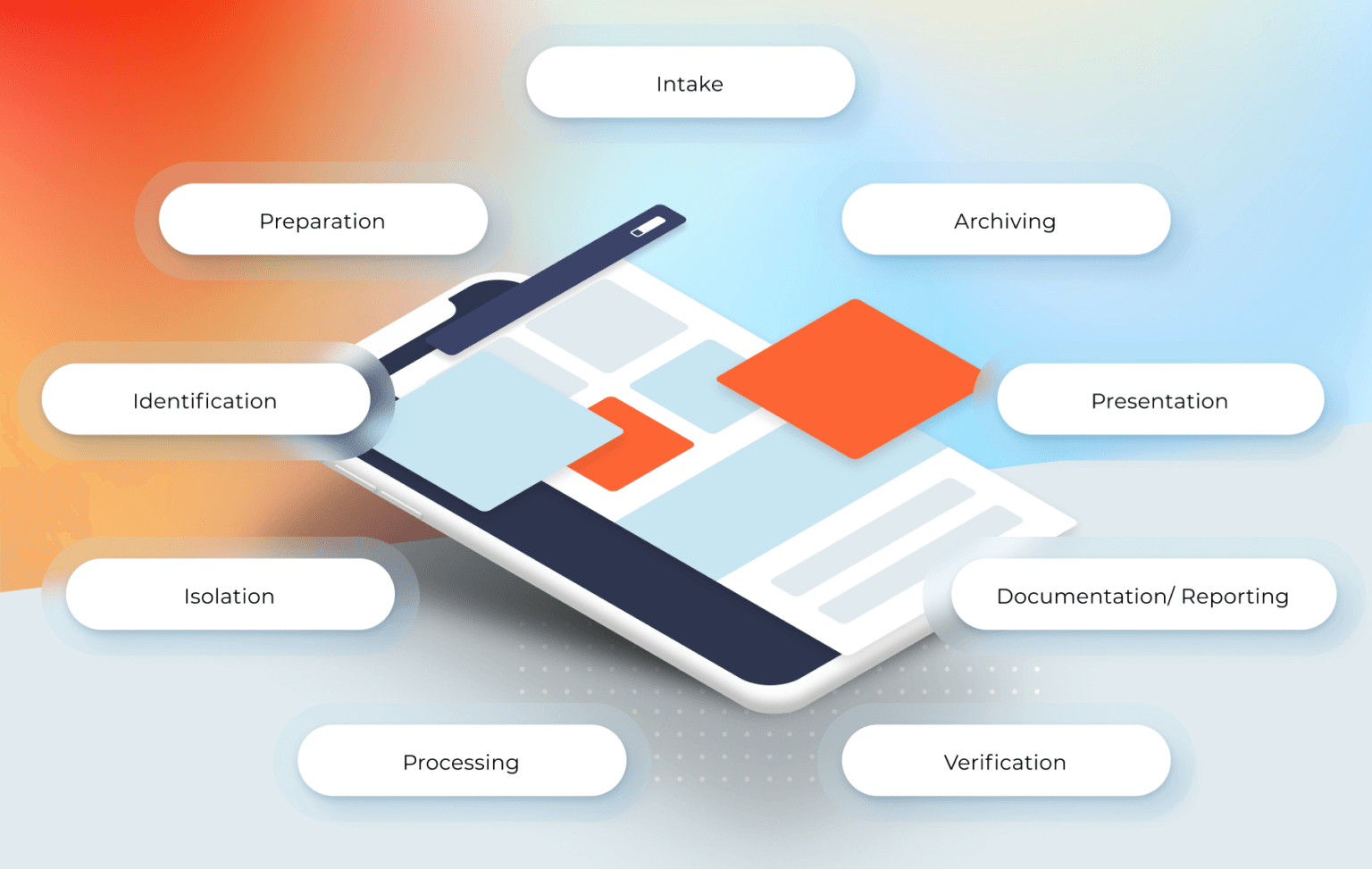
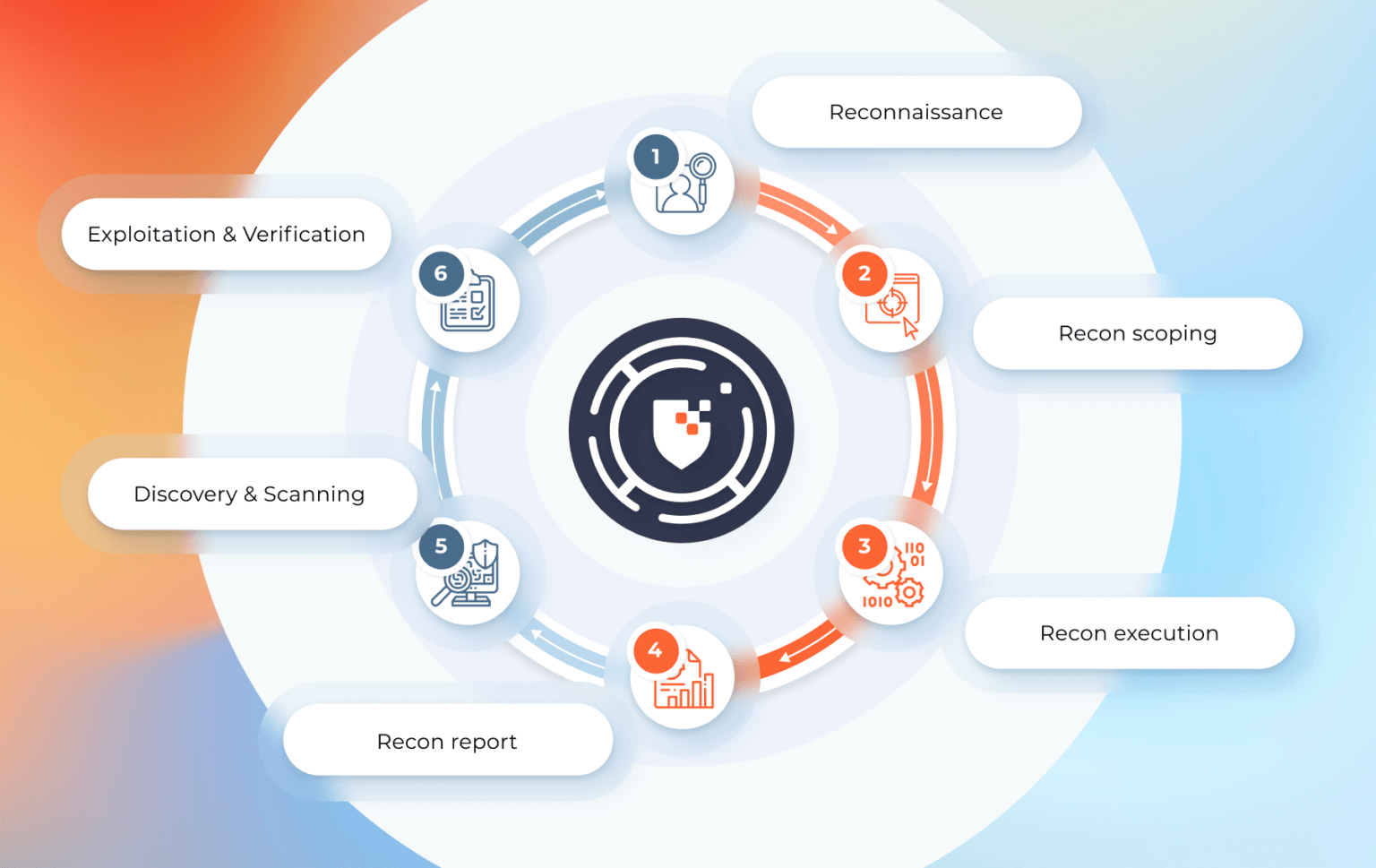
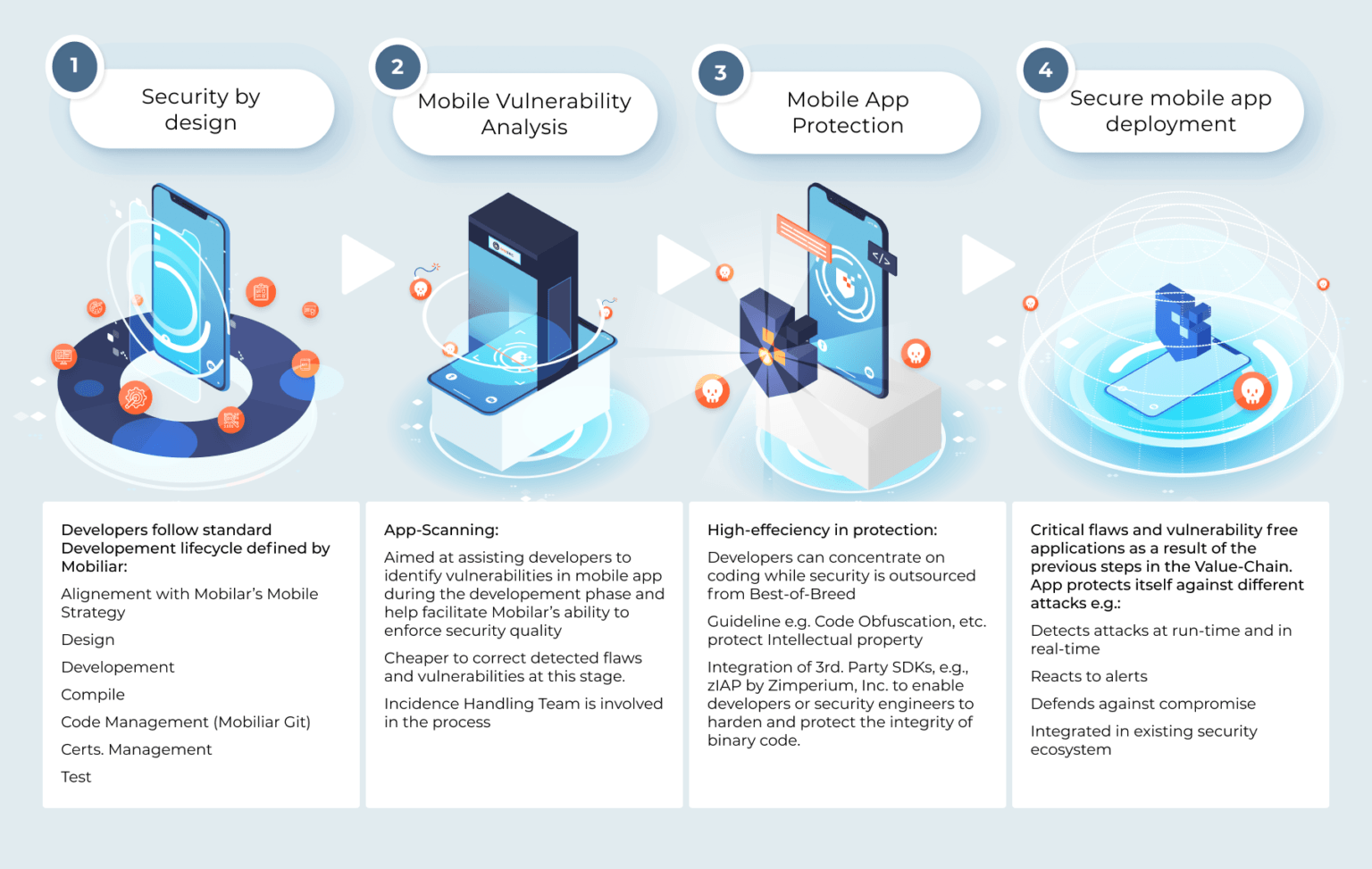
Services
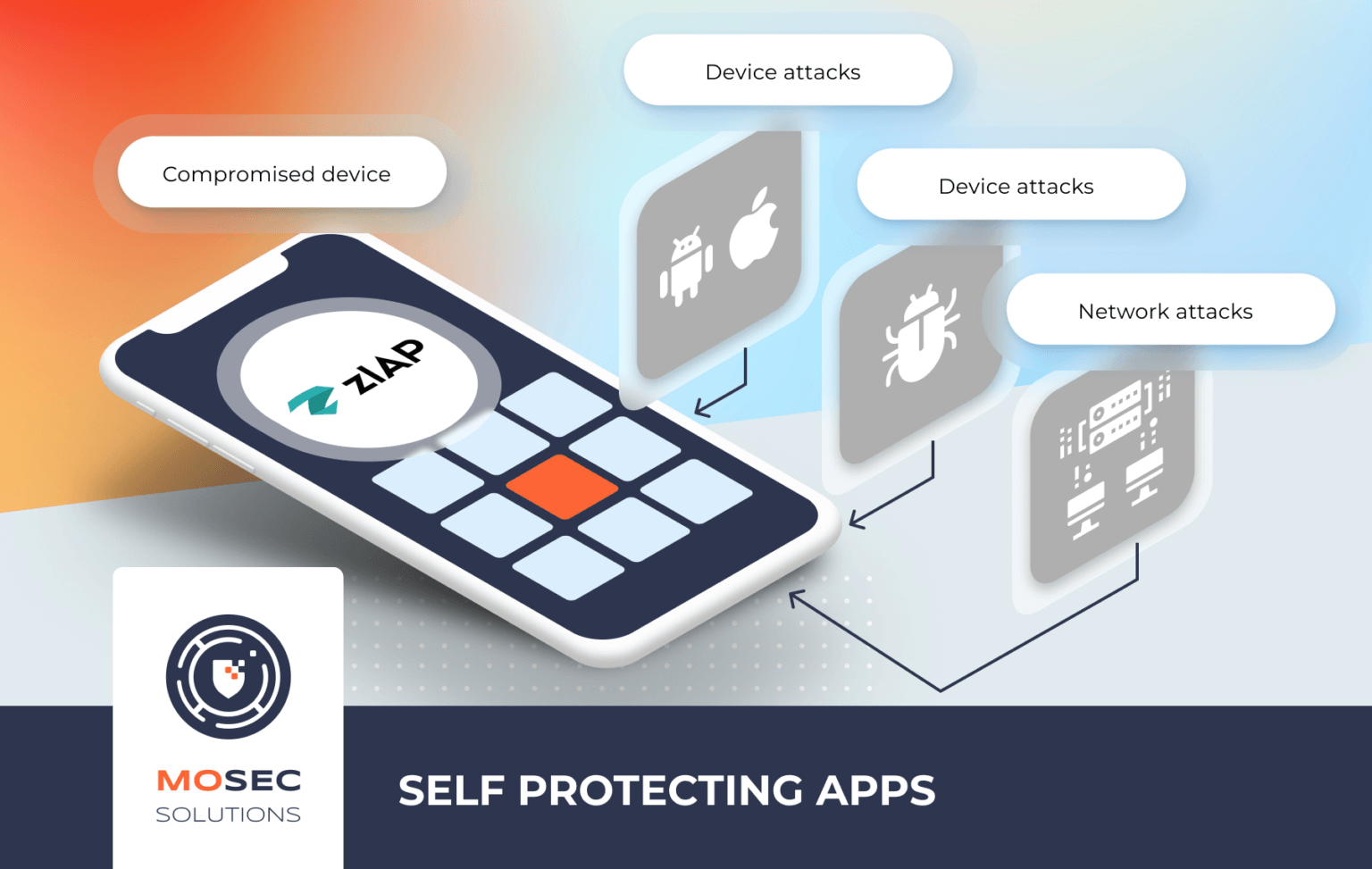
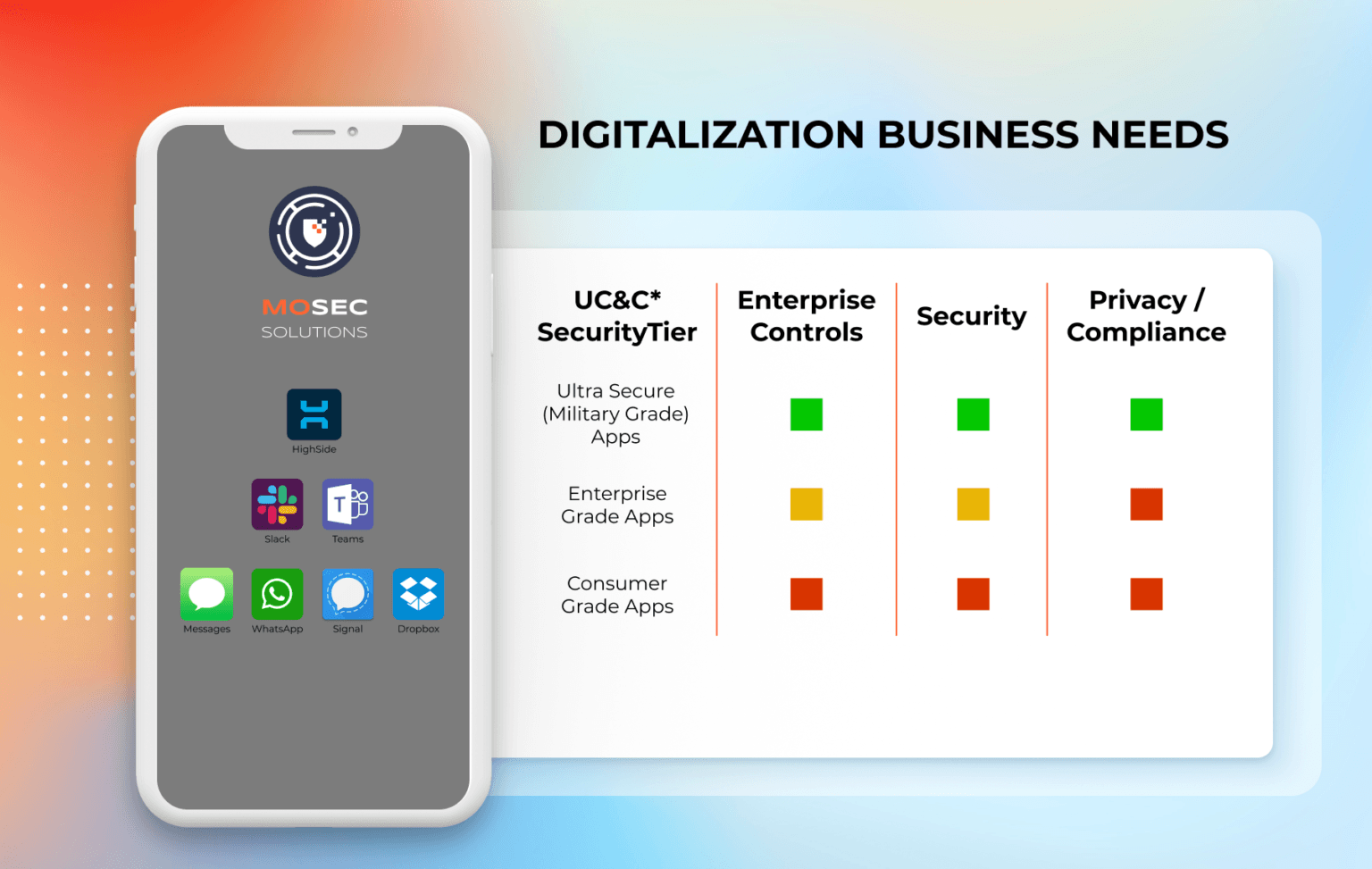
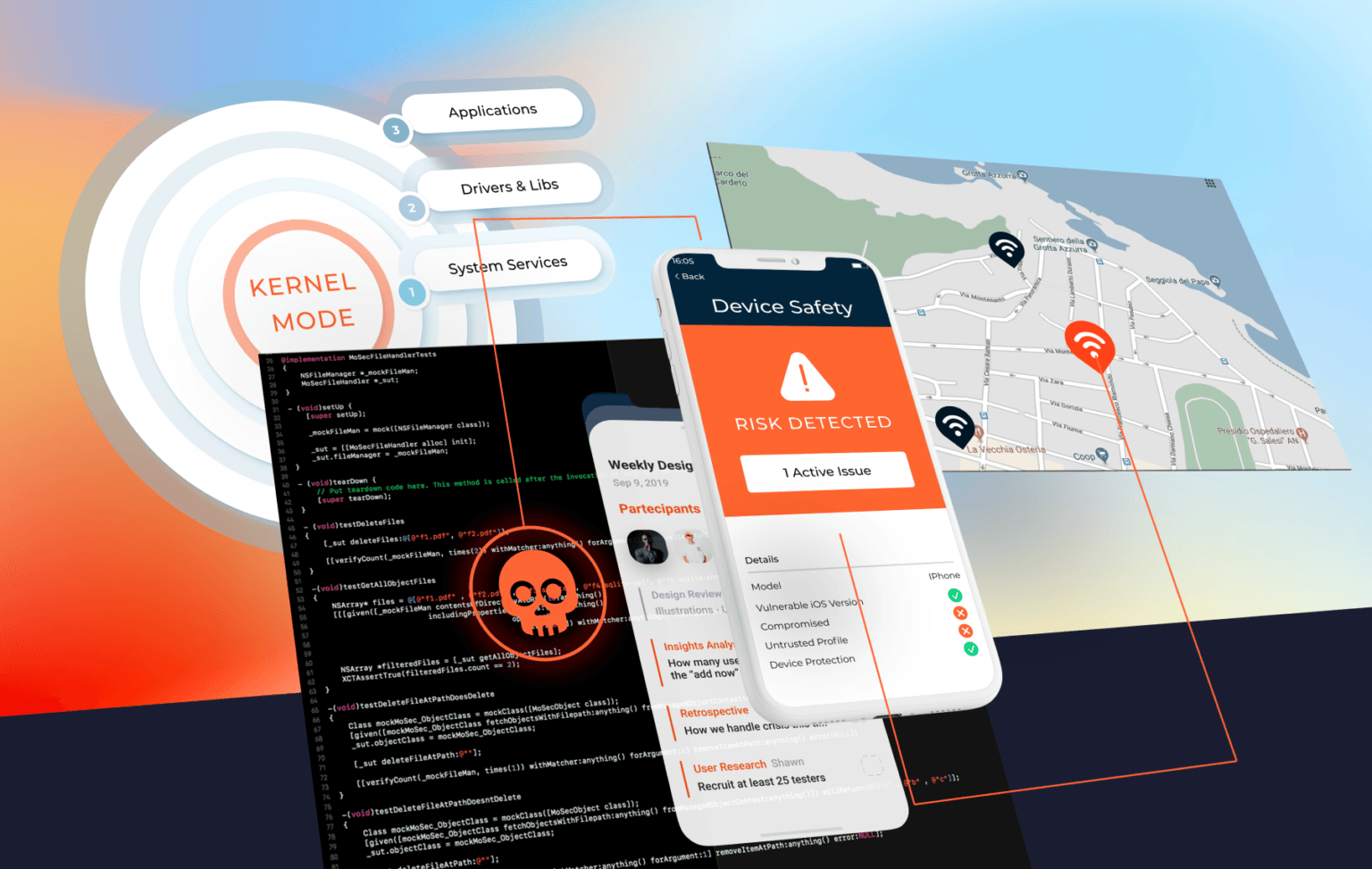
Our services are tightly knit and aligned to our approach towards cybersecurity. It borrows mostly from the military grade approach on battle fields by having an offensive approach. Knowing what the adversaries would do while attacking and integrating it in our offensive approach not only strengthen the weakest link in your security defense chain, but also approves to be more cost effective in your cybersecurity strategy.
contact us